Top Five Cybersecurity Threats in 2020

Cybersecurity is critical to our work at Spathe Systems. As part of our DevSecOps Security Protocol Procedure, we transition application developments with security in mind. We know what’s at stake and will always treat our customers with the care they deserve.
People are using the internet a lot more now, and the need for security measures has never been greater. In effect, the COVID-19 pandemic has made us all rely on the internet for business and social needs. With so much of our lives now online, how can we make sure that we stay protected?
Cybercriminals target our passwords, bank accounts, and other private details every day. While they continue to find new ways to steal our information, you can still stay alert. With so many threats out there, here are the top cyberattacks to know by name in 2020:
Ransomware is on the rise.
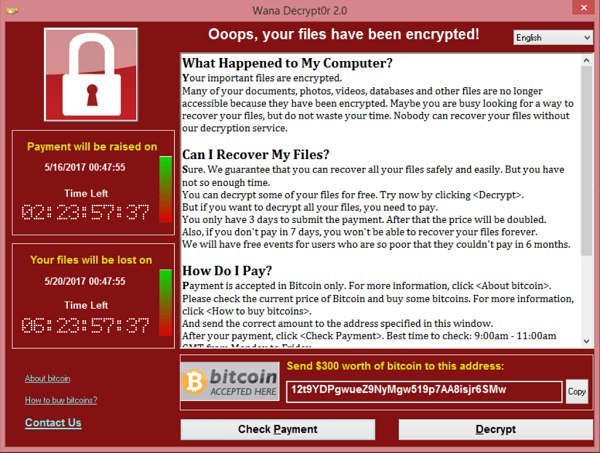
Credit: www.spinbackup.com
Cybercriminals use malicious software (malware) and ransomware to trick users into handing over information. Often hidden in emails, ransomware infects your device and holds your information until you make a payment. Even if you do pay, there is no guarantee they will let your data go.
While you might not be able to prevent all attacks, there are a few precautions that can help.
Be aware of suspicious emails and never download links unless they’re from a trusted source. Having antivirus programs installed, and making sure they stay updated, will help protect you from pop-ups and viruses. It’s also important to regularly back up your information so that you can restore files if they become corrupted.
Most importantly, never pay the ransom; this only encourages attackers.
Here are some of the top reported ransomware attackers and the impacts they had on victims:
WannaCry (2017) – $140,000
CryptoLocker (2013) – $3,000,000
Ryuk (2018) – $3,700,000
Cerber (2016) – $6,900,000
Locky (2016) – $7,800,000
Phishing techniques advance.
In 2019, the FBI reported that phishing was the most prevalent crime type used to steal private information. Cybercriminals pretend to be businesses or company owners and ‘phish’ for private details. Like ransomware, phishers will email their victims but may pretend to be someone they might know.

Credit: us.norton.com
Recently, phishers have started targeting mobile apps. While mobile app developers have upped their security game, you can still take extra steps for added protection.
Phishing attackers usually ask the victim to complete a task for them. Because they look real, victims will respond with private details and risk their entire security network. Often times, phishing emails are poorly constructed with spelling and grammar issues – a key indicator of a harmful message. You can learn how to better identify a threat by examining five key indicators of a phishing email.
Again, never hand over any private information through email, phone, or instant messages. If something looks like it’s from your employer, check with them to make sure.
Viruses take aim at your entire network of devices.
Internet of Things – or IoT – is the system that we use to connect our devices. Most appliances like smart homes, fitness watches, and Wi-Fi enabled devices are all part of the IoT. If your device connects to the internet, it is likely part of the IoT.
While being able to connect more devices has improved many things, cyber experts see it as potential risk. IoT is a target because of its central layout, and the number of devices in the infrastructure. Cybercriminals can gain access to an entire system of devices just by attacking their common Wi-Fi network.
The best way to prevent an IoT attack is to monitor your devices and networks. This can be as simple as checking a device’s network security settings once a month. A strong password can also help secure your devices and networks from a potential hack.
Lastly, always be aware of the networks you connect to. Do not join a public network unless you have security systems in place to keep track of them.
 Cryptojacking: How cryptocurrencies are vulnerable.
Cryptojacking: How cryptocurrencies are vulnerable.
Cryptojacking is “the unauthorized use of someone else’s computer to mine cryptocurrency,” according to CSO. Like ransomware and phishing, cryptojackers hide in email links. Once clicked, malware begins secretly mining for cryptocurrencies without the user even knowing.
Mining for cryptocurrency requires a lot of computer processing power which is why hackers target personal systems. By piggybacking on their computer’s power source, cryptojackers can make money while the user goes about their business online. This often leads to a slower, more sluggish system which can be extremely damaging for businesses.
Just like with other techniques, the best way to avoid a cryptojacking attack is to ignore suspicious emails and downloads. Additionally, you can download certain programs that specialize in blocking cryptojacking scripts.
Social media and the risk of your information.
Social media is not a brand-new concept, but its increasing influence on our lives raises some red flags. The biggest concern with social media is its access to user information. Details like your phone number, email address, home address, and more are all potential targets.
Certain platforms can even collect private details, like your browsing history, while you’re logged in. Facebook, for example, uses this information to target ads to your account which many see as an invasion of privacy. If you don’t want social platforms using this information, you can learn how to update your privacy settings here.
One of the biggest social media issues was the 2018 Facebook-Cambridge Analytica data scandal. Millions of users had their information unknowingly breached by one of Facebook’s partnering companies. Facebook admitted to using the personal data for over 87 million users making it one of the largest leaks in history.
While this was a major case, it’s important to understand that data harvesting happens everywhere. When dealing with social media, there are certain steps you can take to protect your information. Connect only with people you know and trust. Limit the amount of personal details you share on social media, such as your current location. Lastly, continue to monitor your privacy settings to make sure no information is taken from you.
We believe in practicing cybersecurity efforts everywhere.When working from home, make sure that your network is private and not accessible by others. Protect all sensitive information with strong passwords and never share these details through email or messaging platforms.
Security systems provide safe, downloadable programs that can easily track potential threats. These programs will block unsafe websites, pop-ups, and spam emails to help further protect your information. Many providers also have mobile apps that monitor safe Wi-Fi networks and protects against viruses on your cell phone. Simply having these programs installed could save you from a potentially damaging hack.
It is all of our responsibility to protect personal information. By practicing better security practices at work and at home, we help ensure confidentiality and sensitivity of information. For more information on our cybersecurity efforts, visit www.spathesystems.com.







